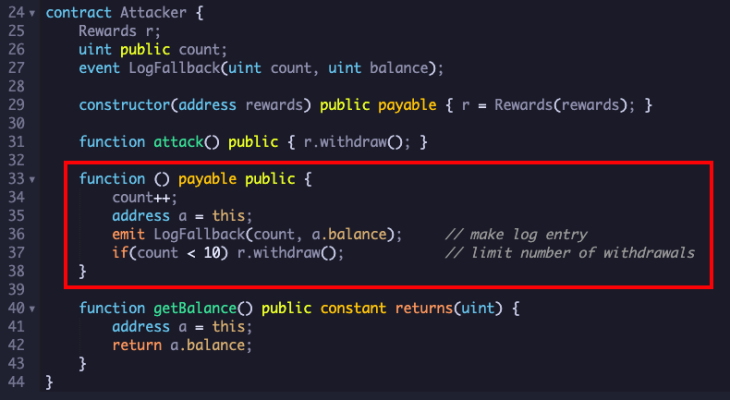
A reentrancy is a type of exploit used to drain funds from a smart contract. It occurs when a contract function recursively calls another function before the first function has finished executing. This allows the attacker to call the first function again before the first function’s changes are committed.
Reentrancy attack are conceivable on the grounds that Robustness savvy contracts are not string safe. This implies that various capabilities can be executing simultaneously, and the request wherein they execute isn’t ensured.
Reentrancy patterns in Solidity
There are two main types of reentrancy patterns in Solidity:
-
Post-withdrawal reentrancy: When a function withdraws funds from a contract and then calls another function before the withdrawal is complete, this occurs. The attacker can then use the first function to withdraw more funds, despite the fact that the balance has already been reduced.
-
Self-destruct reentrancy: This happens when a function calls the selfdestruct() function, which destroys the contract. The attacker can then call the function again before the contract is destroyed, gaining access to its state and funds.
Tips to avoid reentrancy attacks
- Before withdrawing funds, use the require() statement to check the contract’s balance. The attacker will be prevented from withdrawing more funds than are available.
- If an unexpected condition is met, use the revert() statement to revert the contract’s state. This can be used to stop an attacker from running malicious code.
- The Check-Effects-Interactions (CEI) pattern should be used. This pattern ensures that all state changes occur prior to any external calls. This makes exploiting reentrancy vulnerabilities more difficult for the attacker.
def withdraw(amount):
balance = self.balance
require(balance >= amount)
self.balance -= amount
send(amount)
This code takes money from the contract's balance and transfers it to the caller. The require() statement ensures that the balance is greater than or equal to the amount withdrawn, preventing the attacker from withdrawing more money than is available.
Conclusion:
Reentrancy attacks are a serious security vulnerability in Solidity smart contracts. By following the tips above, you can help to protect your contracts from these attacks.
Advertisement